Amazon.com: Penetration Testing: A Hands-On Introduction to Hacking: 0884600461290: Weidman, Georgia: Books

Amazon.com: Penetration Testing: A Hands-On Introduction to Hacking: 0884600461290: Weidman, Georgia: Books
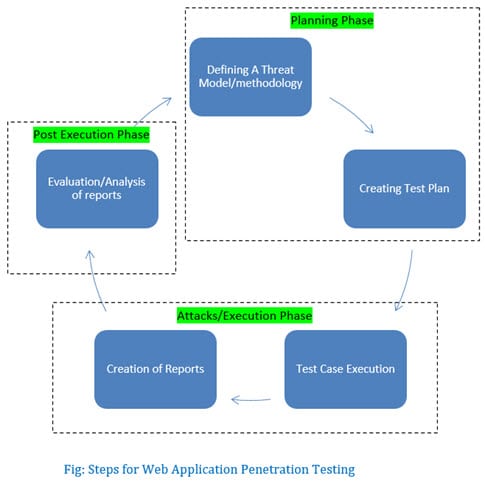
![Web application hacking methodology - Mastering Kali Linux for Advanced Penetration Testing - Third Edition [Book] Web application hacking methodology - Mastering Kali Linux for Advanced Penetration Testing - Third Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781789340563/files/assets/adbe6b83-bf2c-46dd-bbcf-712159e13def.png)
Web application hacking methodology - Mastering Kali Linux for Advanced Penetration Testing - Third Edition [Book]

Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks