
Characteristics and types of Penetration testing in computer science | Informatica e Ingegneria Online

What Is Penetration Testing? Why Your Business Needs Penetration Testing? | Managed IT Services and Cyber Security Services Company - Teceze







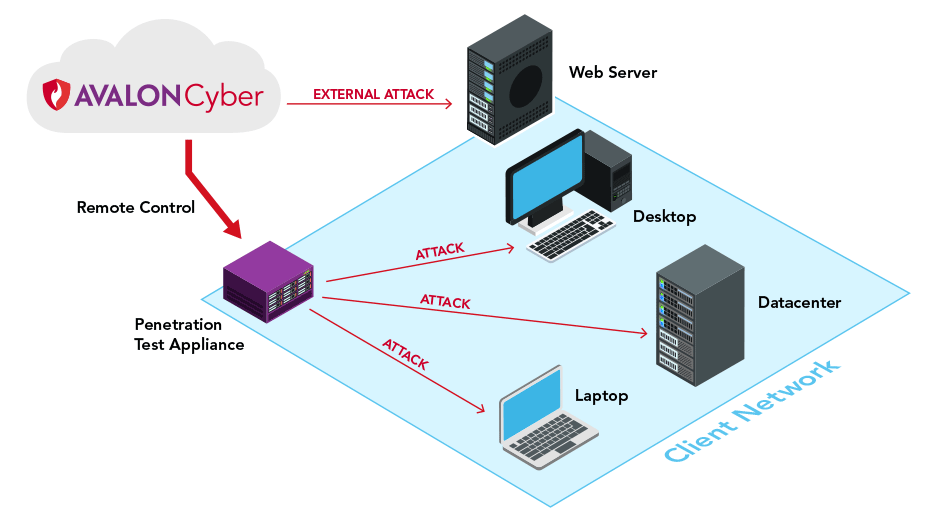













![Penetration Testing [Pen Test]: Types, Methodology & Stages Penetration Testing [Pen Test]: Types, Methodology & Stages](https://d2o2utebsixu4k.cloudfront.net/media/images/41ec9496-81c9-4786-9b7c-e49b83286728.png)