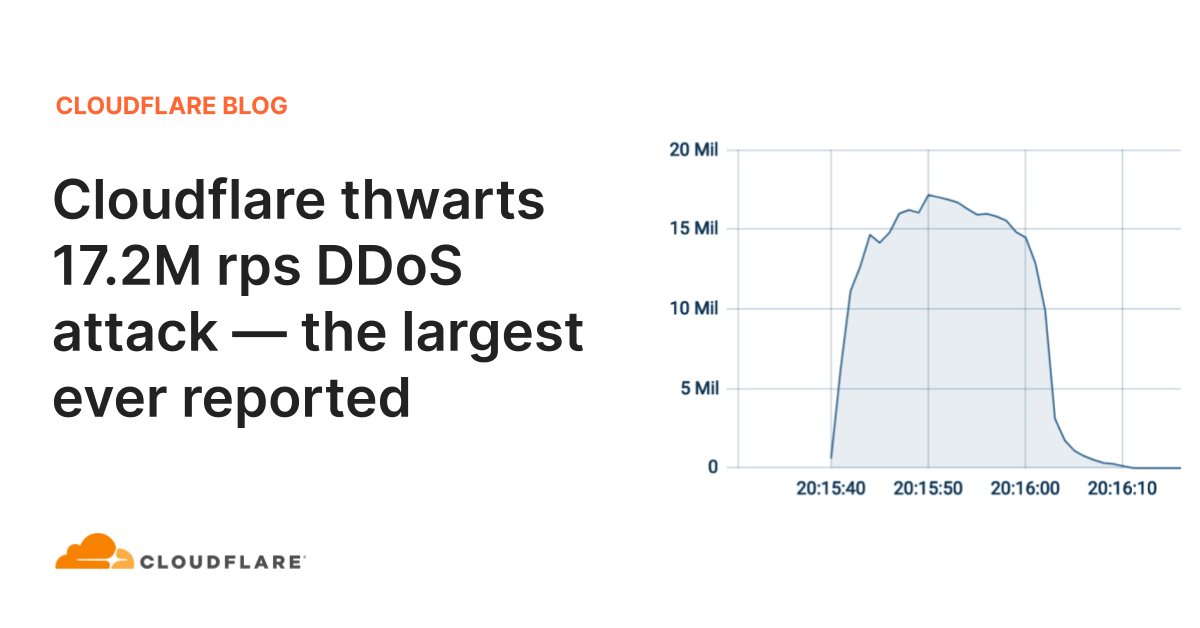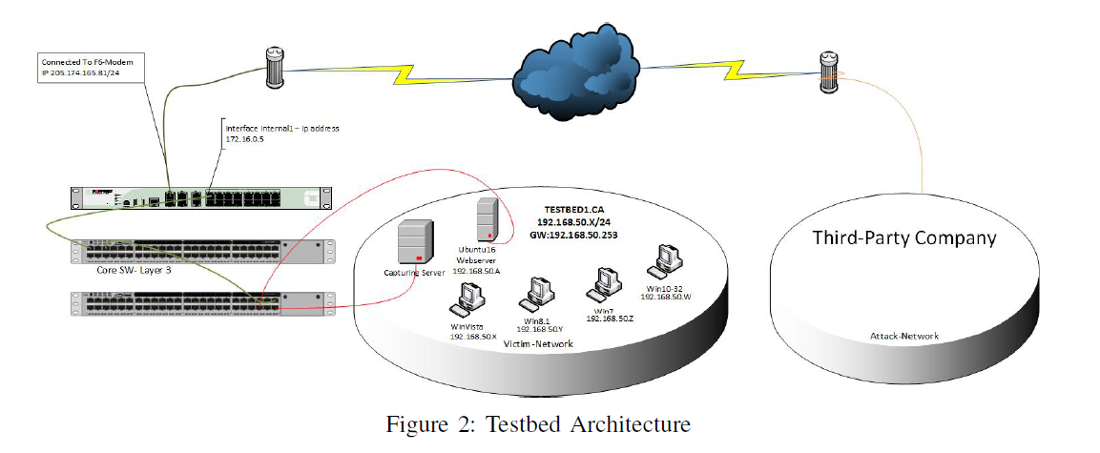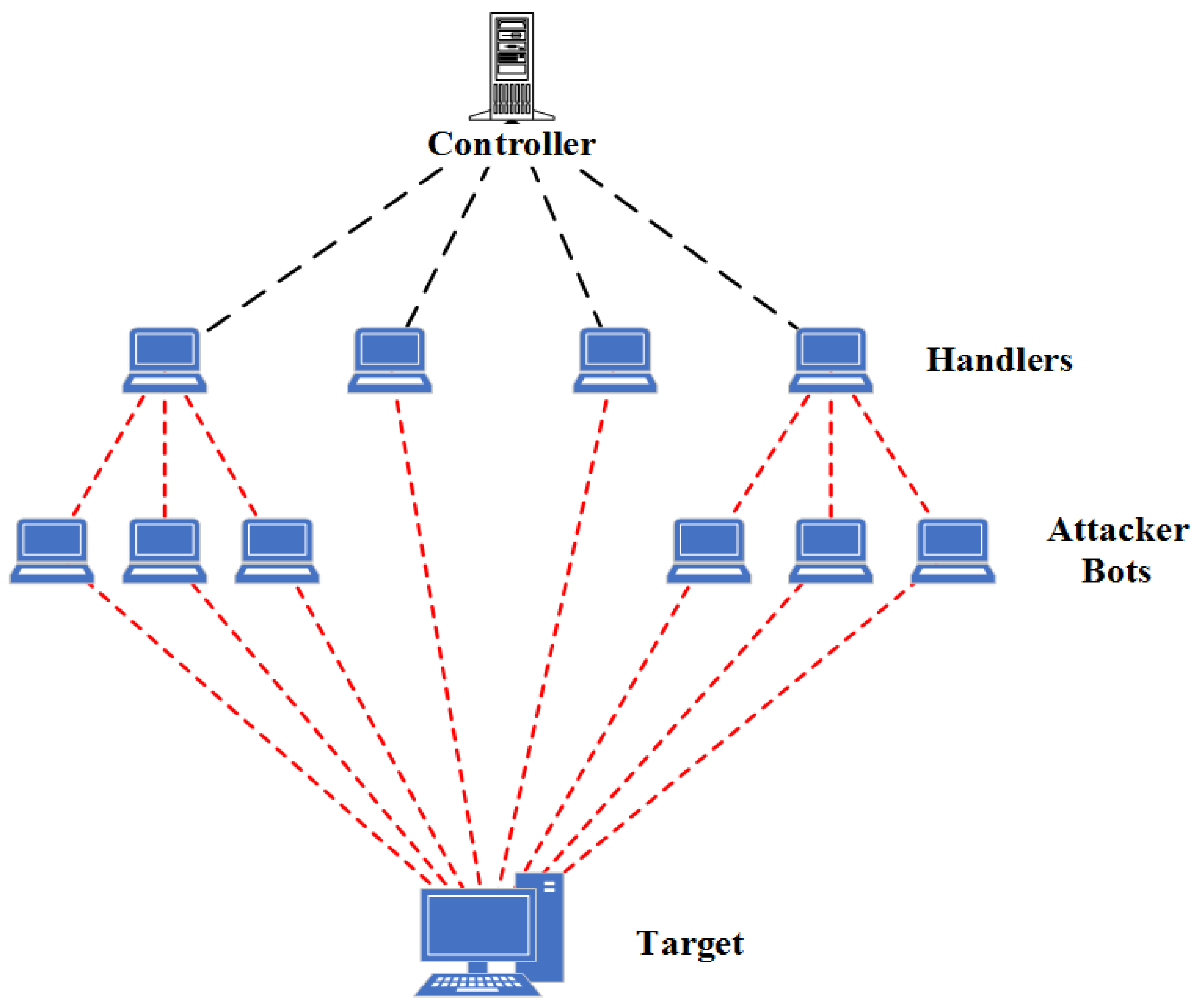
Future Internet | Free Full-Text | Effective and Efficient DDoS Attack Detection Using Deep Learning Algorithm, Multi-Layer Perceptron
18 Hours of Disruption: How DDoS Attacks Plagued PokerStars' High Profile WCOOP Series | Poker Industry PRO
Ddos Attack Color Icon Vector Illustration Stock Illustration - Illustration of bomb, virus: 206757301
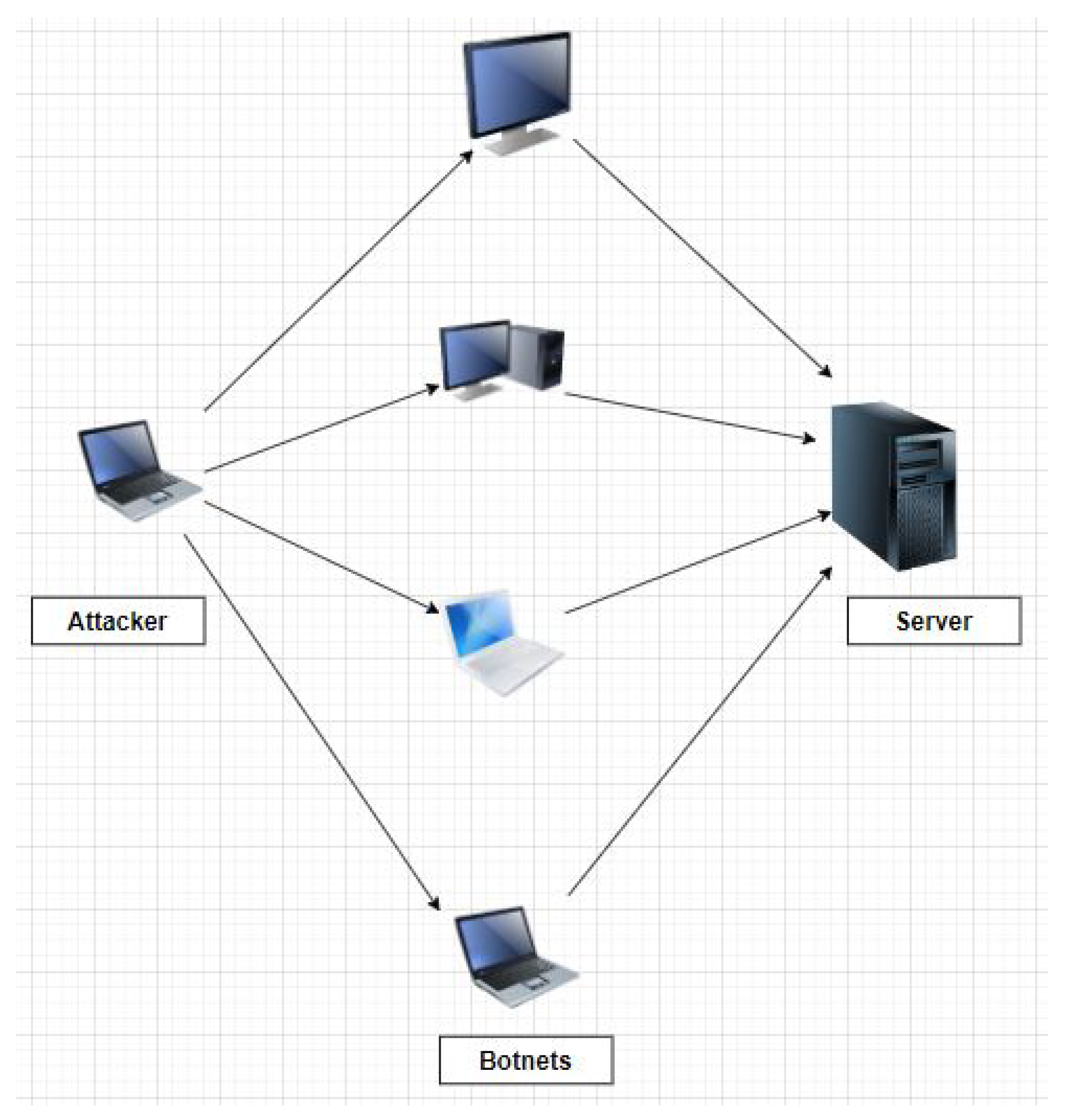
Computers | Free Full-Text | Explainable AI-Based DDOS Attack Identification Method for IoT Networks