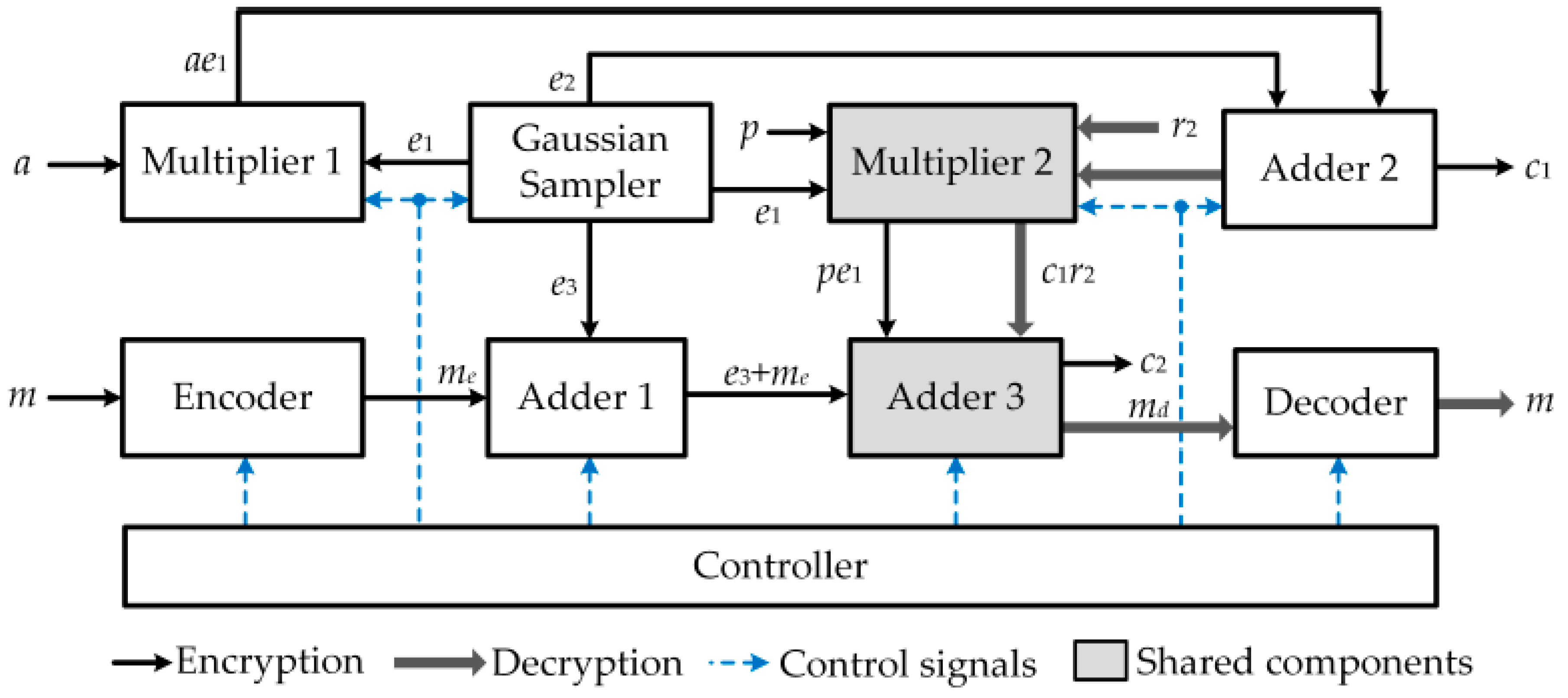
Electronics | Free Full-Text | High Efficiency Ring-LWE Cryptoprocessor Using Shared Arithmetic Components

Electronics | Free Full-Text | Efficient-Scheduling Parallel Multiplier-Based Ring-LWE Cryptoprocessors

Learning With Errors and Ring Learning With Errors | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
GitHub - CMMayer/Toolkit-for-Ring-LWE-v1.0: Implementation of a toolkit for ring-LWE based cryptography in arbitrary cyclotomic number fields.
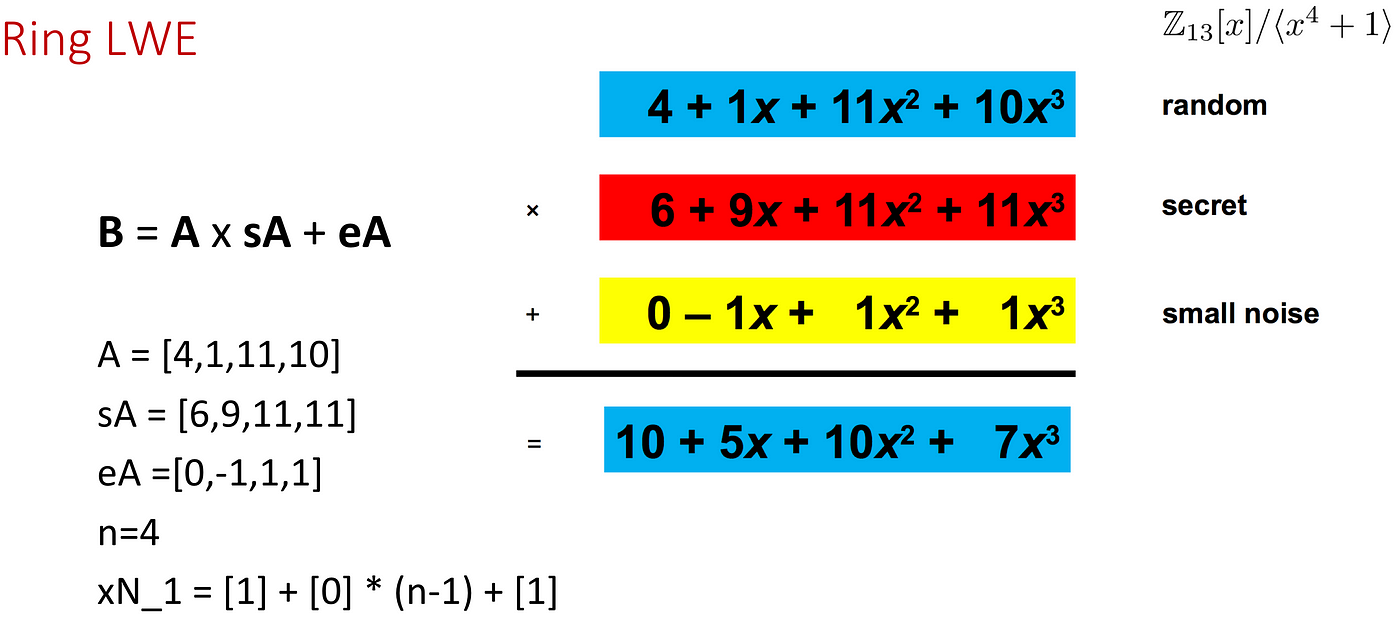
Learning With Errors and Ring Learning With Errors | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
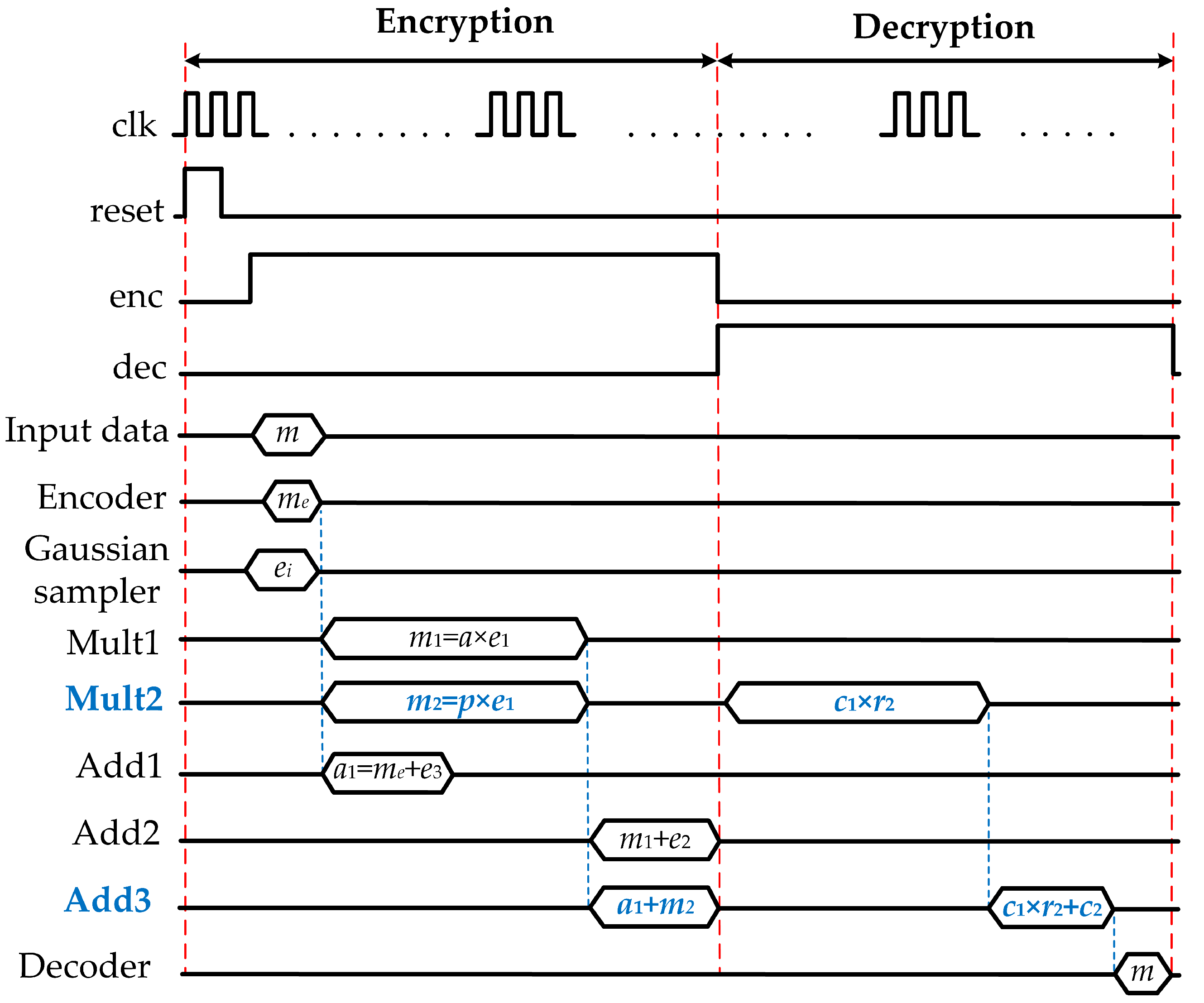
Electronics | Free Full-Text | High Efficiency Ring-LWE Cryptoprocessor Using Shared Arithmetic Components


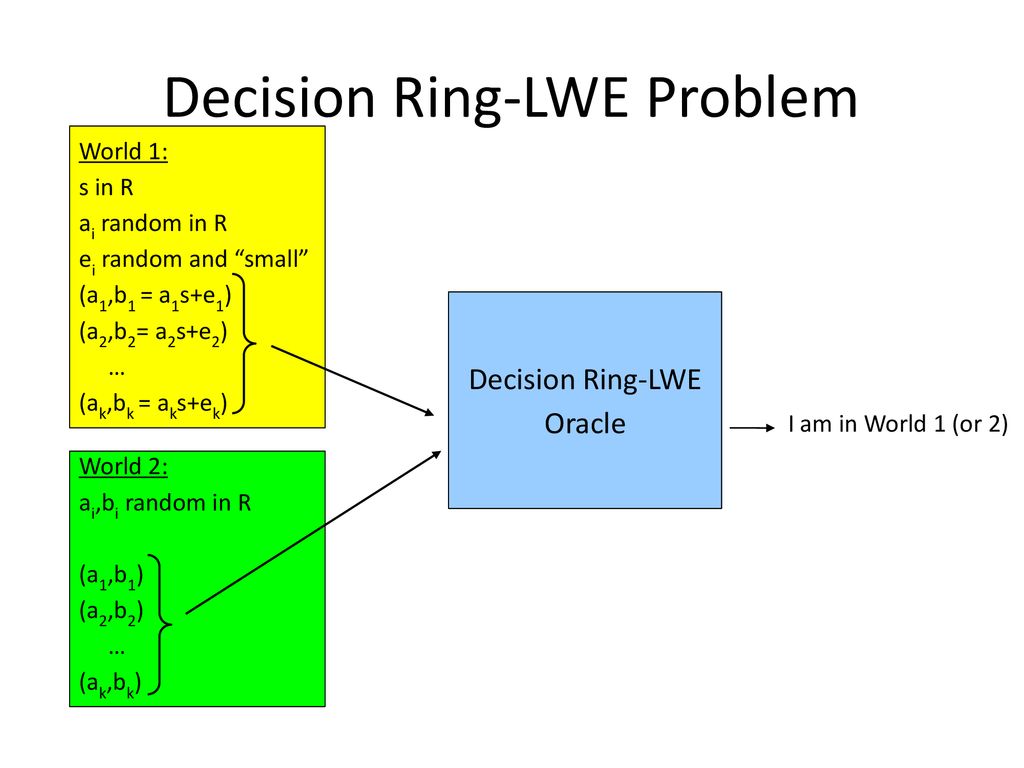




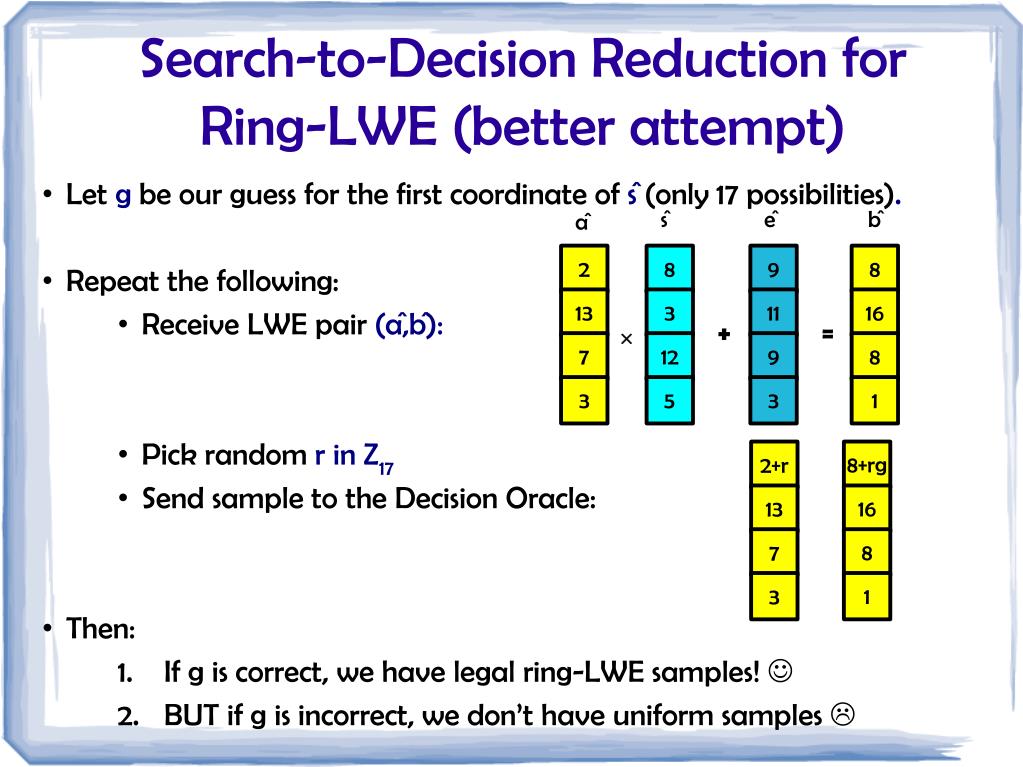

![PDF] Module-LWE versus Ring-LWE, Revisited | Semantic Scholar PDF] Module-LWE versus Ring-LWE, Revisited | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7f0b73dcb090e90962042ef64cd1d162893cfff7/3-Figure1-1.png)

![PDF] Efficient-Scheduling Parallel Multiplier-Based Ring-LWE Cryptoprocessors | Semantic Scholar PDF] Efficient-Scheduling Parallel Multiplier-Based Ring-LWE Cryptoprocessors | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6741ac510c265f29ac7baae64fc8f07a56aa2db5/2-Figure1-1.png)


