Anonymous Ghostwriters - Rubber Hose Cryptography works by filling the entire hard drive with random characters that are indistinguishable from encrypted data. The file system then takes each archive of real data

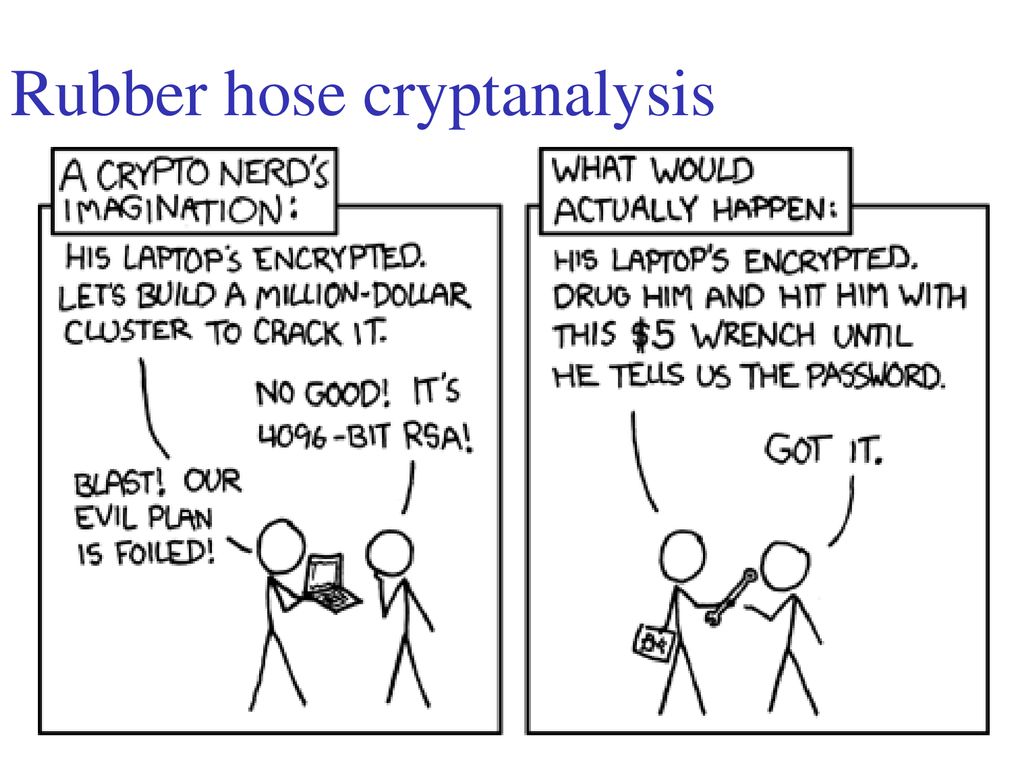
Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks A Paper by Hristo Bojinov, Daniel Sanchez, Paul Reber, - ppt download

Peter Leimbigler on Twitter: "@austwitnerd @ZachWeiner Conventionally known as rubber-hose cryptanalysis, which is very computationally inexpensive: https://t.co/ZpxKVWWQBh" / Twitter
Reframing how you think about the concept of “managing your private keys” – Corey Petty's Personal Website

Programmer Humor on Twitter: "Cryptography: expectations vs. reality https://t.co/RD8Tfg057p https://t.co/IpB6X3VFtz" / Twitter

Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks A Paper by Hristo Bojinov, Daniel Sanchez, Paul Reber, - ppt download